My small business has been using Absolute Telnet for many years, mostly for ssh2 connections, but only recently have we started to be required to use hardware token authentications (Yubikey is the one we have been suggested to use the most often recently). While we are able to easily turn on the hardware token authentication support in Absolute Telnet for the initial linux login and that works fine, we are being told that we also need to enable some type of “forwarding” so that it can be used when sudo commands are issued as well within the shell. THAT we do not know how to set up and are hoping you can provide some guidance.
The customers we have worked with keep telling us to use tools like Putty CAC or Mobaxterm that also support forwarding via the putty agent (pagent) which then forwards to the Yubikey PIN entry for the sudo command as well, but they are not able to give us guidance how to facilitate this in Absolute Telnet. We seem to have found entries in your changelog years ago in version 9.x (we are running 11.x) that forwarding was supported, but it does not tell us how to enable it for this purpose.
How do we manually add a smartcard to an agent so that it then has the requests for sudo commands forwarded on?
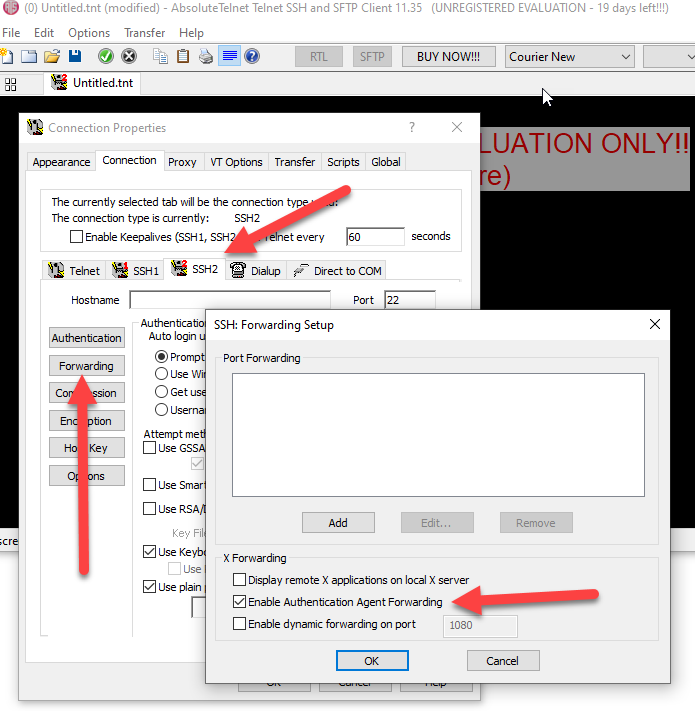
Agent forwarding is enabled under Options/Properties/Connection/SSH2/Forwarding
1. Enable it (and save your config)
2. Logout and back in
3. At the command line, type the command 'ssh-add -l' and you should see the fingerprint of your hardware key
If the above works, the key is available for forwarding. There may be some command line work to USE it, especially with SUDO, but whatever your other people are doing should work now.
I already had that box checked, but I unchecked, rechecked it, and saved it again just to be safe. The command you provided does not return a good good response (I do not see a fingerprint), even though I had to have my Yubikey in the USB slot and specify the PIN for my Yubikey in the Windows Security Smart Card popup during the initial login. Here's the sequence of events I see at the linux command line:
Connecting to sigmadev.xxx.edu:22
attempting xxx.yy.z.136:22... Success!
First key exchange completed.
Negotiated Algorithms:
Key exchange : ecdh-sha2-nistp521
Host Key : ssh-ed25519
Session encryption : aes128-cbc
MAC : hmac-sha2-512
Compression : none
Username: asits
Accessing SmartCard key for authentication
Authentication SUCCESS
Allocating PTY... SUCCESS
Start X11 forwarding... Skipped
Starting authentication agent... SUCCESS
Starting shell... SUCCESS
Last login: Tue Jan 24 16:00:09 2023 from 10.100.233.111
[asits@sigmadevxxx ~]$ ssh-add -l
error fetching identities for protocol 1: agent refused operation
error fetching identities for protocol 2: invalid format
The agent has no identities.
[asits@sigmadevxxx ~]$
When I login via putty, also entering the Yubikey PIN when prompted, and then issue the ssh-add -l command I get a fingerprint returned. What am I doing wrong?
Thanks.
Andy
I have a Yubikey, so I can do some testing.
Which version of Absolute are you running? You mention 11.x, but there have been a few revisions to 11.
Also, which SSH server and version?
Brian
I am running Absolute Telnet version 11.21, Winsock 2.0.
The machine I am connected to has OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017.
Let me know if there is anything else I can provide.
Andy
I downloaded and installed version 11.35 of Absolute Telnet and received the exact same error as previously described when I try the ssh-add -l command.
ssh-add -l
error fetching identities for protocol 1: agent refused operation
error fetching identities for protocol 2: invalid format
The agent has no identities.
When I login via putty, this command returns a fingerprint.
Andy
In case it helps, I have attached the documentation that I built with the institution's help to use the Yubikey to accomplish the login and sudo work to their linux box via ssh. They wanted me to use Putty CAC and pagaent, but I would rather use Absolute Telnet! But the method described here does work. Please do not publicly post this attached document to the forum.
Andy
I am attaching here a document that I developed with the institution I am trying to connect to. It describes a connection method that does work with Putty CAC + pagaent + Yubikey. Perhaps this will give you some clues since this does work for a competing product. But I would rather use Absolute Telnet. Please do not publicly post this document to the forum.
Andy
Having a heck of a time getting the file I want to get you attached. Trying again...
I am attaching here a document that I developed with the institution I am trying to connect to. It describes a connection method that does work with Putty CAC + pagaent + Yubikey. Perhaps this will give you some clues since this does work for a competing product. But I would rather use Absolute Telnet. Please do not publicly post this document to the forum.
Andy
I would like to provide you a copy of a document that I developed with the institution I am trying to connect to. It describes the setup for the connection method that does work with Putty CAC + pagaent + Yubikey. Perhaps this will give you some clues since this shows how the process works for a competing product. But I would rather use Absolute Telnet. Since the document is apparently too large to post to the forum (120KB size is pretty small...) I will send it separately to your email.
Andy
I tried Absolute Telnet version 11.36 that you made available and the results now ultimately seem good, but I do not know how to interpret the first message when I issue the ssh-add -l command:
[asits@xxxxxxxxxx ~]$ ssh-add -l
error fetching identities for protocol 1: agent refused operation
2048 SHA256:**yv+0rOk*********RxFuWT******* asprague (RSA)
Note: I replaced part of the server name with x’s and some of the fingerprint bytes with * characters
Despite the “error fetching identities for protocol 1” that showed up, the sudo command I needed to issue succeeded after I ran the ssh-add -l command the first time and then exited Absolute Telnet and logged back in again. This is a very clean process compared to the somewhat more complex one they suggested using putty CRC and the separate pageant. The only thing that one might consider a bonus about their approach was that a dialog box pops up when I issue the sudo command to confirm that I am aware that access to the hardware security token (Yubikey) has been requested by the process and I am OK with that being used. I have to click “OK” or something like that to authorize it. Some might find that nice.
Very cool! Thanks for the tweak. We have multiple licenses of Absolute Telnet, but we have fewer people using it than in the past, so let me get a count of users so I know how many we need to purchase an upgrade for.
Andy
Andy and I worked on this and found a bug in the authentication agent. Modifications had been made to the agent protocol on the server side that broke the AbsoluteTelnet/SSH implementation. It would get confused and then stop working. Please download 11.36 or higher
From version history:
Changes made in version 11.36(January 26, 2023)
- Fixed bug in agent forwarding that prevented it from working with smart cards